Dark web monitoring tools are more important than ever in the age of cyber terrorism, corporate data theft, and personal privacy invasion. Having the right dark web monitoring tools can make all the difference in protecting your business. If you are looking for resources to help get started, here are some of the most popular Dark Web Monitoring Tools of 2018.
Locating activity happening on dark web networks is no easy task. To help you monitor dark web activity, this post includes the top 14 best dark web monitoring tools to use in your business.
The top14 Best dark web monitoring tools include:
- CrowdStrike Falcon X Recon
- Echosec Beacon
- DarkOwl Vision
- SpyCloud ATO Prevention
- Alert Logic Dark Web Scanner
- Webhose.Io
- Argos
- Lastpass
- Progress WhatsUp Gold
- ACID Cyber Intelligence
- Digital Shadows SearchLight
- DigitalStakeout Scout
- Recorded Future
- SpyCloud ATO Prevention
CrowdStrike Falcon X Recon (FREE TRIAL)

Falcon X Recon is a research service that scours Dark Web sources for mentions of your company’s assets. These include brands, corporate identities, the email addresses of people within your business, and mentions of key executives and employees.
The information that you receive from this service offers a double check on PII security. Key information on your customers should be kept safe. However, if PII is stolen from your business, it is likely to end up for sale on the Dark Web. Knowledge of this leak should have been caught by your data loss prevention system. However, if you don’t have data protection in place, the Falcon X Recon service gives you a chance to catch up.
Falcon X Recon is a subscription service and part of the CrowdStrike family of products that are offered from their Falcon SaaS platform. You don’t have to download and install any software in order to use the Falcon X Recon service. You can start on a 15-day free trial.
Echosec Beacon

Echosec Beacon is a Dark Web scanner. It can hunt down compromised credentials, disclosed personal information and stolen financial data that is available in various locations on the internet.
This is an online service that operates like a search engine. The user enters a name, a social security number, or an email address and then searches through sources in Dark Web marketplace, social media sites, and forms to find incidences of those details up for sale, or openly appearing on free lists.
The tool will also look for websites that mention the named person – information about people is collected for “doxing,” which gathers information to enable a charlatan to either target or impersonate that person in a phishing attack.
The service can identify data breaches and search out malicious information stores that hold data on businesses as well as individuals.
DarkOwl Vision

Vision, by DarkOwl, is a Dark Web scan tool that indexes the content of malicious sites all over the World Wide Web to identify data stolen from its clients.
The Vision system searches for mentions of the client company’s domain and email addresses in hacker data exchanges. The search is an automated process. This information is constantly updated by repeated scans and those disclosures are made available in the dashboard for those subscribing companies to which the data pertains.
The DarkOwl vision system is integrated into a package of intelligence services, called Darkint Suite. Another element in this suite is Darkint Score, which is a vulnerability assessment of the client company’s exposure to Dark Web data loss.
Darkint Suite’s data feeds can be integrated into applications through an API. The DarkOwl service is a threat intelligence database; it does not monitor infrastructure or network traffic. Companies subscribing to DarkOwl will also need threat protection and data loss protection software to fully protect their systems.
SpyCloud ATO Prevention

SpyCloud offers two services for account takeover (ATO) prevention – one to cover the employees of companies and the other to protect the customers of online services.
ATO protection concentrates on protecting the accounts that businesses set up for access to their resources, such as network logins or user accounts at websites. A major part of the service involves detecting accounts that have already been compromised.
The ATO prevention service includes a cloud-based threat intelligence database, which warns clients of compromised accounts. The information on disclosed credentials is discovered by a Dark Web scanning tool. Other elements in the threat intelligence system include known sources of phishing and impersonation attacks, which gives the protecting agent software guidance on which incoming emails to block.
The service also proactively monitors Active Directory and sets up stronger password policies, such as password rotation and enforced password complexity.
Alert Logic Dark Web Scanner

The Dark Web Scanner from Alert Logic is an account takeover prevention system. The service scans the Web for account credential disclosure and compiles a list of compromised accounts that pertain to the client. One worrying aspect of this service is that the report of at-risk accounts is sent once a month, which means that the information about vulnerable accounts might arrive too late.
The service doesn’t look for disclosures of personal or financial information of individuals that might be held on the servers of the client company. However, the Dark Web Scanner is just part of a package of system protection measures offered by Alert Logic. The service is included in the Alert Logic Enterprise edition, which is available on a 30-day free trial.
Webhose.Io
Webhose.Io helps IT teams transform unorganized data into readable data that can be read in machines for optimized solutions. Webhose.Io has 33 employees and earns annual revenue of $4.8 million.
Argos
Argos provides IT teams with digital risk management software that prepares them for any cyberattack by analyzing cyber threats. Argos has 4,699 employees and earns annual revenue of $1.06 billion.
Lastpass
With over 25 million users, LastPass guarantees protection even if the user is not logged in. It monitors accounts and sends an alert if any information appears to be compromised. The platform offers dark web monitoring as part of their LastPass Security Dashboard. It gives an overview of the health and security of the customer’s stored accounts. With a zero-knowledge security infrastructure, the platform continuously monitors email addresses within a database of breached credentials. Lastpass offers its services to 70,000 businesses, including The New York Times, Mashable, and CNN Money.
Progress WhatsUp Gold
Progress offers a network monitoring system WhatsUp Gold that installs in a Windows server, letting companies find and fix network problems. The core module of this platform is a network device monitor that can be enhanced by several add-on modules such as the Network Traffic Analyser (NTA). The NTA or Flow Monitoring can identify traffic to known dark web entry and exit nodes. It can also identify traffic to specific suspicious IP lists. Progress allows customers to have a personal list of suspicious IP addresses. They are alerted when users or applications on the network attempt to access them or the dark web and respond immediately. The 2021 Network Monitoring Emotional Footprint Champion offers a free trial as well.
ACID Cyber Intelligence

The ACID Cyber Intelligence service gathers threat intelligence from social networks, criminal sites, chat systems, the Deep Web, and the Dark Web. The information found from these sources allows the service to warn its customers of any threats that may be about to occur and also of any data leaks that have occurred.
The data searches are performed by web bots and so they continue to operate around the clock. The data type that the threat intelligence system looks for include account credentials, e-mail addresses and email contents, domain names, payment card data, intellectual property, insider information, personal information about employees, and mentions of the company and its employees in the context of threats.
Customers of the service get access to an account-protected dashboard where alerts are displayed when cyber threat intelligence related to that has been identified. This information is sent to the console as soon as it is encountered and it is also sent to a key contact at the client company via email.
Digital Shadows SearchLight
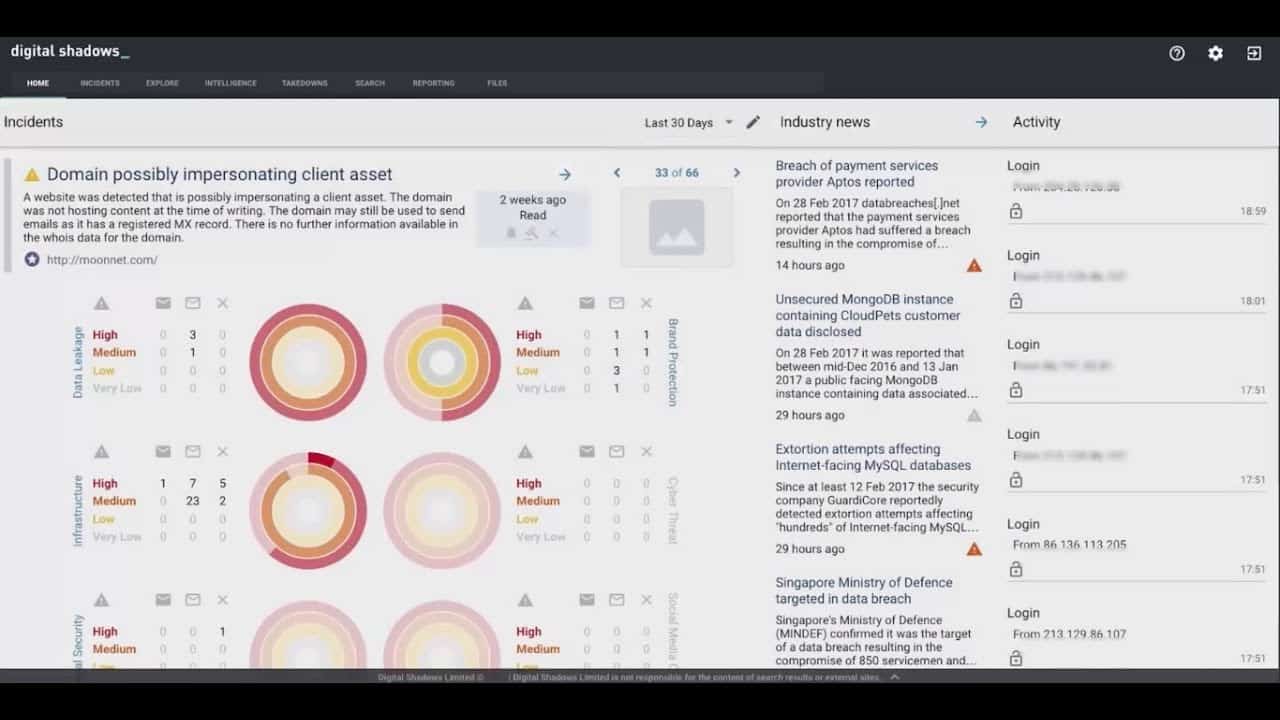
Digital Shadows is particularly concerned with protecting the brand and reputation of the companies that use its services. Rather than focusing on account protection, this service protects both the image and trade secrets of the companies that it serves.
Key Features
- Discovers patents and trade secrets
- Corporate layouts and access codes
- Brand protection
For example, the SearchLight looks for company procedural documents, site plans, and internal memos that have found their way onto other sites that are known for trading in corporate data illegally. One incident that the Digital Shadows site recounts is its discovery of ATM designs that it alerted one of its clients about. That client was the bank that used the compromised ATM design.
Although the service doesn’t look for all user account details, it does scour illegal sites for the disclosure of privileged credentials, such as the usernames and passwords of network administrator or DBA accounts. Digital Shadows offers a 7-day free trial of SearchLight.
Pros:
- Can protect image copyright and trade secrets
- Looks for usernames, passwords, and other indicators of compromise
- Uses visualizations to help highlight key insights
Cons:
- Doesn’t include threat protection software
DigitalStakeout Scout
Scout, from DigitalStakeout, is a Dark Web threat intelligence service. The system includes workflows and machine learning to detect anomalous behavior on the network. It then references the external source or destination of that internet traffic with its Dark Web Scanner and threat intelligence database to identify the malicious actor participating in the suspicious activity.
Key Features
- Detects attacks on networks
- Traces attack sources
- Brand protection
As such, Scout is a data loss prevention system and an insider threat protector as well as a threat-protection system. Scout doesn’t include any remediation procedures. When a Dark Web threat is spotted, Scout raises an alert in the monitoring dashboard. It is up to the network administrator to shut down the traffic either manually or by deploying threat mitigation software.
The service also protects the brands and reputation of customers by scanning all websites for harmful content about those companies. The relevant source and text of the discovered content is then posted in the Scout dashboard.
Pros:
- Intellectual property protection
- Brand defense
- Suggests remediation actions
Cons:
- No remediation procedures
Recorded Future
With actionable intelligence at scale, delivered in real-time, Recorded Future combines automated analytics with human expertise to the various open-source, dark web, technical sources, and original research. The platform provides companies’ security teams, holding over a billion intelligence cards, with all the required information to amplify their security programs. The platform’s machine learning and natural language processing instantly creates links from sites on the dark web to other threat sources, enabling companies to identify quickly, profile, and mitigate risks. Some of their global clients include Accenture, Fujitsu, GAP, McAfee, and Dupont.
SpyCloud ATO Prevention
This security software has recovered over 135 billion breach assets. No wonder, Spycloud is a Gartner Cool Vendor in Identity Access Management and Fraud Detection. SpyCloud also proactively monitors Active Directory and sets up more robust password policies, such as password rotation and enforced password complexity. Taking cybersecurity a step ahead of dark web monitoring, the platform leverages human intelligence to infiltrate criminal communities and gain access to breach data that isn’t available otherwise. It gives enterprises greater — and faster — visibility of exposed credentials and PII that threaten the security of their users’ accounts. Some of their global customers include Cisco, Samsonite, and Avast.
The Different Types of Dark Web Monitoring
There are different types of dark web monitoring tools, each with its own strengths and weaknesses. Here are the four most common types:
1. Web Application Security Scanner: A web application security scanner can identify vulnerabilities in web applications and track any changes to the code. This type of tool is helpful for detecting potentially vulnerable online services and finding malicious actors trying to attack them.
2. Deep Packet Inspection (DPI): DPI tools can identify specific traffic patterns and attacks being conducted on a network. They’re often used to identify and block malicious traffic before it reaches user devices.
3. URL Profiling: URL profiling tools can determine which websites users are visiting based on their unique URL addresses. This information can be valuable for identifying illegal or malicious content or activities, as well as potential sources of data theft or infiltration.
4. Malware Analysis: Malware analysis tools can detect and analyze malware samples in order to find vulnerable files or networks that may be targeted by attackers. These programs can also help defenders prevent attacks from happening in the first place by identifying suspicious files or activity before it occurs.
Advantages and Disadvantages of using Dark Web Monitoring Tools
There are many advantages and disadvantages to using dark web monitoring tools. One of the main advantages is that these tools can help track down illicit activity on the dark web. Additionally, these tools can be used to identify threats and vulnerabilities on the dark web.
One of the main disadvantages of using dark web monitoring tools is that they can be difficult to use. Additionally, these tools may not be as accurate as other monitoring methods.
Top 10 Dark Web Monitoring Tools
There are a variety of different Dark Web Monitoring tools available on the internet. These tools can be used to monitor websites and applications that are located on the Dark Web. Some popular Dark Web Monitoring tools include:
1. Netsparker: Netsparker is a popular tool that is used to scan for vulnerabilities on websites and applications located on the Dark Web.
2. BlackHole: BlackHole is another popular tool that is used to scan for malicious content and activities on websites and applications located on the Dark Web.
3. Website Auditor: Website Auditor is a free tool that is used to audit website security vulnerabilities and issues.
4. W3AF: W3AF is a powerful open source security assessment tool that can be used to scan for web application vulnerabilities, threats, and attacks.
5. SSLScanner: SSLScanner is a freetoolthat can beusedtocontrolinsecureconnectionsonwebsitesandapplicationslocatedonthedarkweb.
6. FireEye ThreatSeeker Advisor: FireEye ThreatSeeker Advisor is an advanced threat detection platform that can beusedtoidentifyandanalyzethreatsrelatedtodomainattacks,spider attacks,SQL Injection attacks, Cross-Site Request Forgery (CSRF) attacks, and more…
Conclusion
If you need dark web monitoring tools then these ones should help you to get started, if you know of other dark web monitoring services then please add them to the comments section for this page.
