Penetration testing (pentesting) is the practice of exploiting weaknesses or vulnerabilities in order to assess the security or functionality of software, hardware, or systems. This guide gives you some free tools for pentesting. The following list doesn’t claim to include all free tools available for all areas in penetration testing. My aim here, is to provide you with a good starting point. I’ll also show you how to install the tools and use them.
Finding free tools for web penetration testing is always a challenge. Not anymore. This article will cover the best open source tools for web pen testers.
Fiddler
Category: Proxy server application
Fiddler is a freeware web proxy tool that is browser and platform agnostic. It has several features that can help an pen tester. It allows users to debug web traffic from any system (works with almost all operating systems on PCs), smart phone, or tablet. From an pen tester tools standpoint, Fiddler is primarily used to intercept and decrypt HTTPS traffic. As the name suggests, users can fiddle with and inspect that traffic to identify vulnerabilities in the application at hand.
Wireshark
Category: Web vulnerability scanner
Wireshark is an industry standard network protocol analysis tool. The tool essentially captures data packets moving within a network and displays them back to the end user in a human-readable form. Wireshark allows users to capture data via Ethernet, Wi-Fi, Npcap adapter, Bluetooth, and token ring to name the few. It even allows users to capture data from USB-attached network interfaces through USBPcap. Wireshark even comes as a console version with the name ‘tshark.’
Nikto
Category: Web vulnerability scanner
Nikto is another tool that is quite famous within pen testing community. It is an open source pen tester tool available under GPL. Nikto offers multiple options within its interface to run against a host. It probes a host to find potential vulnerabilities such as server misconfiguration, insecure host files and programs, out-of-date programs that might pose risk, and version-specific issues that might risk the server. Nikto is available on OS X by MacNikto.
Burp Suite
Category: Net Scanner
One primary use of the Burp Suite is to intercept all requests and responses between the browser and the target application. The free version is also useful for generating a proof-of-concept cross-site request forgery (CSRF) attack for a given request. There’s also the application-aware crawler that can be used to map out application contents. A paid version unlocks even more features.
Aircrack-ng
Category: Password cracking
Aircrack-ng is a suite of wireless password cracking tools for the 802.11a/b/g family of wireless networks that supports raw monitoring (rfmon) mode. It captures network traffic in monitor mode. Once enough data is captured, it runs cracking algorithms to recover WEP and WPA keys. The Aircrack-ng suite consists of various tools such as Airodump-ng (a packet capturing program), Airsnort-ng (an encryption key cracker), Aireplay-ng (for traffic generation), and Airdecap-ng (a captured file decryption tool).
Karkinos
Karkinos is a lightweight and efficient penetration testing tool that allows you to encode or decode characters, encrypt or decrypt files and text, and perform other security tests. Generally, the Karkinos is a bundle of multiple modules that, when combined, enable you to carry out a wide range of tests from a single tool.
As such, some people refer to it as the ‘Swiss Army Knife’ for penetration testing.

Key features
- Encode or decode characters in several standard formats,
- Crack hashes simultaneously using its built-in wordlist of over editable or replaceable 15 million breached or common passwords.
- Generate popular hashes such as SHA1, SHA256, SHA512, and MD5.
- Compatible with Linux and Windows.
- Interact and capture reverse shells, and more.
Metasploit
Metasploit is an advanced and versatile that helps testers to identify and exploit vulnerabilities. The tool enables you to prioritize while demonstrating the potential risks using a closed-loop vulnerability validation.
Also, the feature-rich tool allows you to perform a wide range of testing that ranges from scanning and creating your payloads to performing exploits and test security awareness using simulated phishing emails.
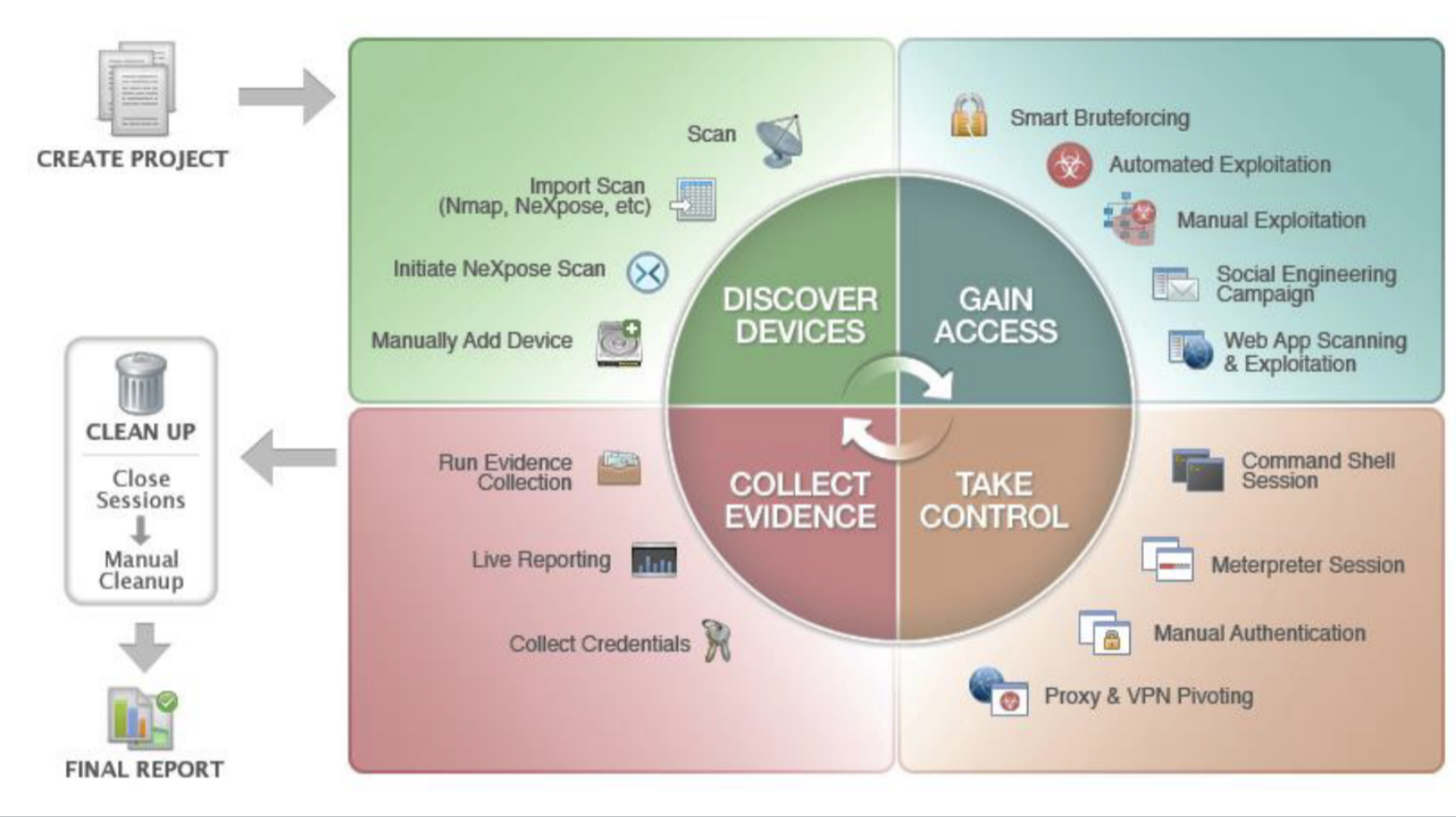
Key features
- It has an in-built discovery scanner for TCP port scanning on the target device. The scanning allows you to gain visibility of the services running on a network and identify open ports and vulnerabilities you can exploit.
- Vulnerability and configuration errors scanner to identify flaws and potential attack vectors
- Automated or manual exploitation of identified vulnerabilities.
- Allows you to access the target through password attack methods such as brute force or reusing credentials.
- Works on Windows, Mac OS, and Linux and available in both command line and GUI-based versions.
Netsparker Security Scanner (GET DEMO)
The Netsparker web application for pen testing is totally automatic. It has become very popular due to the fact that developers can use this on many different platforms for entire websites, including web services and web applications. It can identify everything pen testers need to know to make an informed diagnosis—from SQL injection to cross-site scripting.
Another characteristic that makes this tool so popular is that it allows pen testers to scan up to 1,000 web apps at once while also allowing users to customize security scans to make the process robust and more efficient. The potential impact of vulnerabilities is instantly available; it takes advantage of weak points in a read-only way. This proof-based scanning is guaranteed to be effective, including the production of compliance reports among other great features, including the ability to work with multiple members for collaboration, making it easy to share findings; there’s no need to set up anything extra due to the fact that scanning is automatic.
Key Features
- Fully automated
- Bundle of many tools
- Systems intelligence
- Fast scanner
- Automatic assessment report
Conclusion
Penetration testing is a methodical process. It relies on multiple streams of data in order to gain insight into how much damage can be done to your system. There are numerous source to find free tools for penetration testing. This article will provide recommendations based on the authors’ experience with different tools.
Penetration testing is an important step in validating the security of your web applications. There are many tools available to help with this process. However, many of these tools do not offer source code or require purchasing premium versions at additional costs. This blog post outlines some free tools for carrying out a penetration test against a web application.
